Today, we're excited to announce advanced access management features for the Hightouch platform. With advanced roles, workspace owners can create granular policies governing what actions users can perform across Hightouch resources. Policies can also be conditioned on labels that are attached to specific Hightouch resources like Audiences and syncs. With these industry-leading fine-grained access control features, users can be confident that as they invite more teammates to the platform, they'll be maintaining a proper security posture over their data.
Why Advanced Access Management Matters
Reverse ETL is an incredibly powerful way to activate the data in your warehouse and send it to countless mission-critical business tools. We frequently hear from customers who want to invite more teammates but are worried about the security implications. As one customer put it, "Hightouch is almost too easy to use. Anyone can break anything." The result is sometimes, not all teammates who can benefit from Hightouch are invited.
Governance is especially important for large enterprises dealing with sensitive data like personally identifiable information (PII). Many of our customers have invested in locking down their data warehouses. For example, Snowflake administrators don't want marketing users to access PII or independently send data into downstream systems. With fine-grained controls, our customers can now leverage the policies already built in their source systems.
Our New Access Management Capabilities
Until recently, Hightouch only supported three high-level roles: admin, editor, and viewer. This has been sufficient for smaller Hightouch deployments, but our larger customers have asked for more fine-grained control. Previously, an editor could create and change any resource within Hightouch, which could result in undesired access or system updates.
Now, admins can create custom users and groups and assign them to specific business roles (e.g., marketer). Those roles can then have specific policies assigned to them based on the following:
- Actions represent the tasks that specific roles can perform (e.g., create, read, update, delete, etc.)
- Those actions can be performed on Hightouch resources (sources, destinations, models, syncs, Audiences, and parent models).
- (Optional) Conditions can also be applied to give admins even more granular control over how and when policies are applied (e.g., labeling a sync
project:marketing).
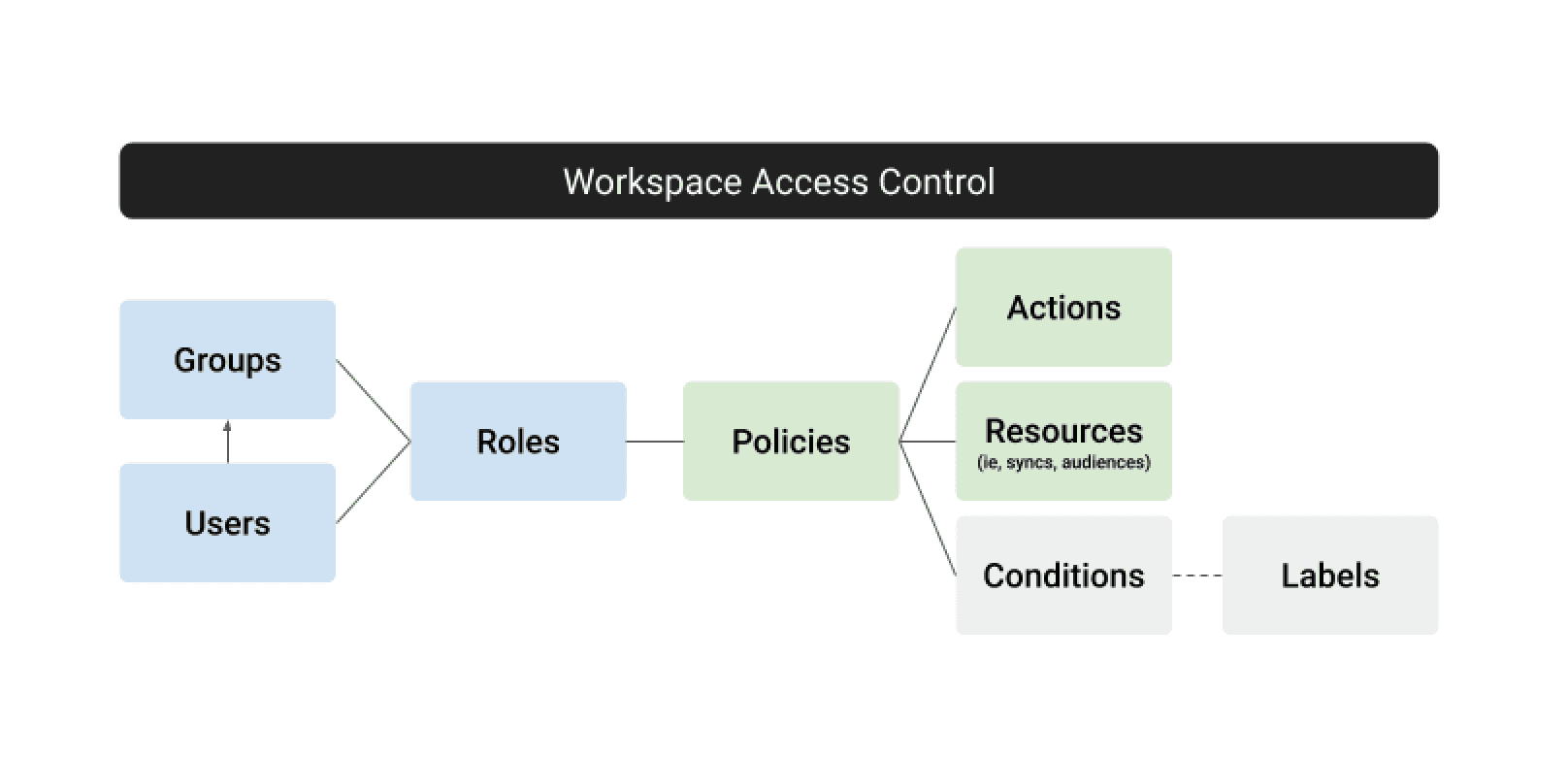
Advanced Access Control in Hightouch
Here are some ways these controls can be customized to solve business use cases:
- Process Enforcement: marketers can create audiences and syncs but cannot access raw data in sources and parent models.
- Visibility and Security: all users can view a critical sync, but only a select group can edit it.
- Data Hygiene: an ad-hoc set of models and syncs for a specific campaign only needs to be shared with the team working on the campaign.
- Resource Protection: a highly privileged Snowflake account can only be viewed by admins and the Hightouch system for syncing purposes.
“Hightouch helps some of the largest companies in the world sync mission-critical data to their business tools. In such high-stakes environments, proper governance is key to protecting against unauthorized data access and user errors that can break the pipeline. With industry-leading granular role-based and label-based access controls, users can be confident that they won't be compromising on security or governance as they invite more users to collaborate.”

Josh Curl
Co-Founder & CTO at Hightouch
An Example of How it Works
Let's say a large consumer enterprise wants to create an "Audience Collaborator" role for marketers who should be able to create Audiences but should not have the ability to change the underlying schema (model).
A workspace admin would create the two policies below:
Policy 1 — Lets user create audiences and syncs for the specific project tagged
- Actions: create, read, update, delete, preview, enable
- Resource: sync, audience, sync template
- Conditions: project is
demand-gen-prod
Policy 2 — Limits the user's ability to change the underlying schema
- Actions: read, preview
- Resource: audience schema
Currently, Hightouch supports these inputs through a JSON format. Soon, we will be releasing a UI for quicker configuration.
Below is the corresponding UI experience for the Audience Collaborator role as compared to the admin view.
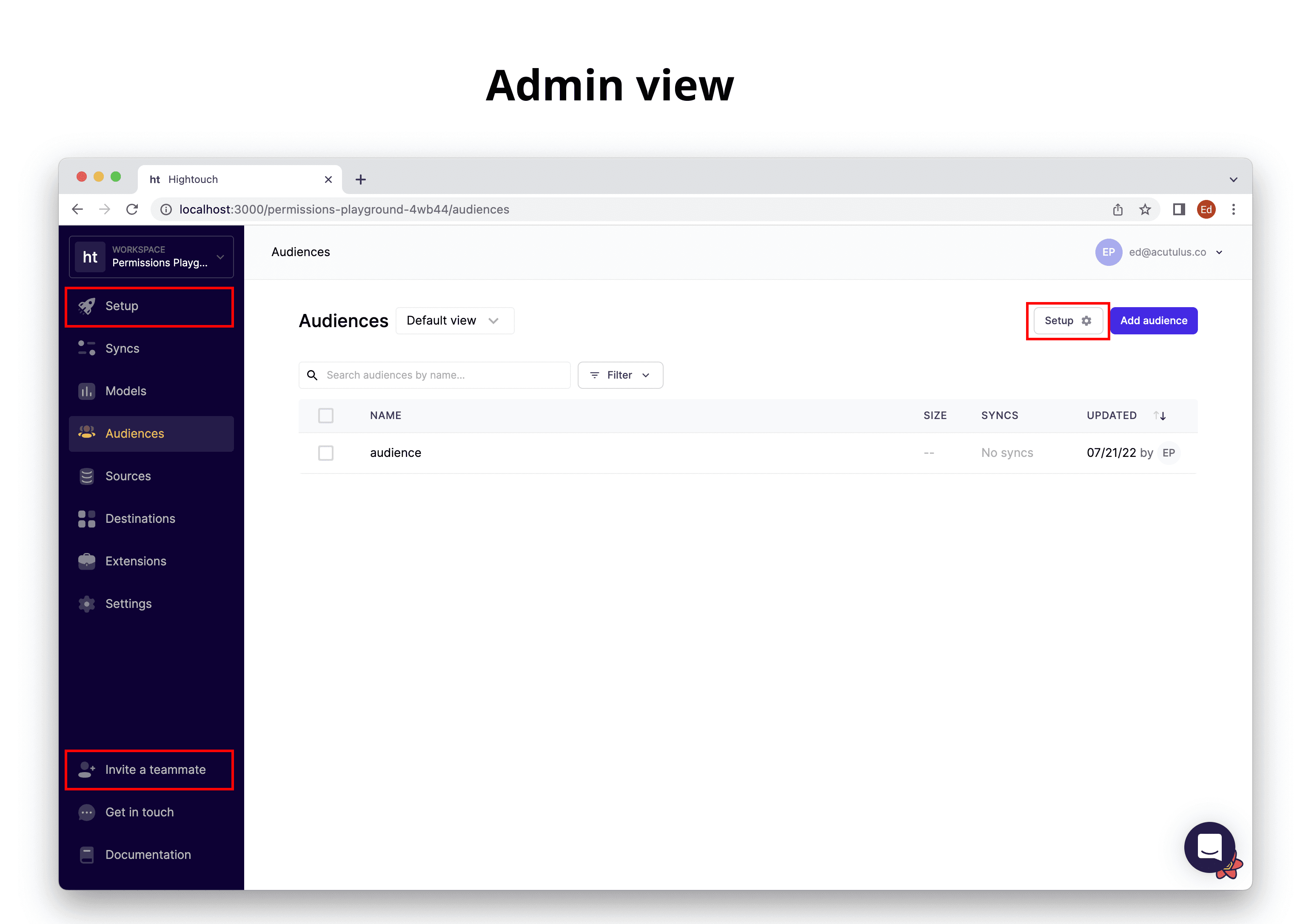
Admin View
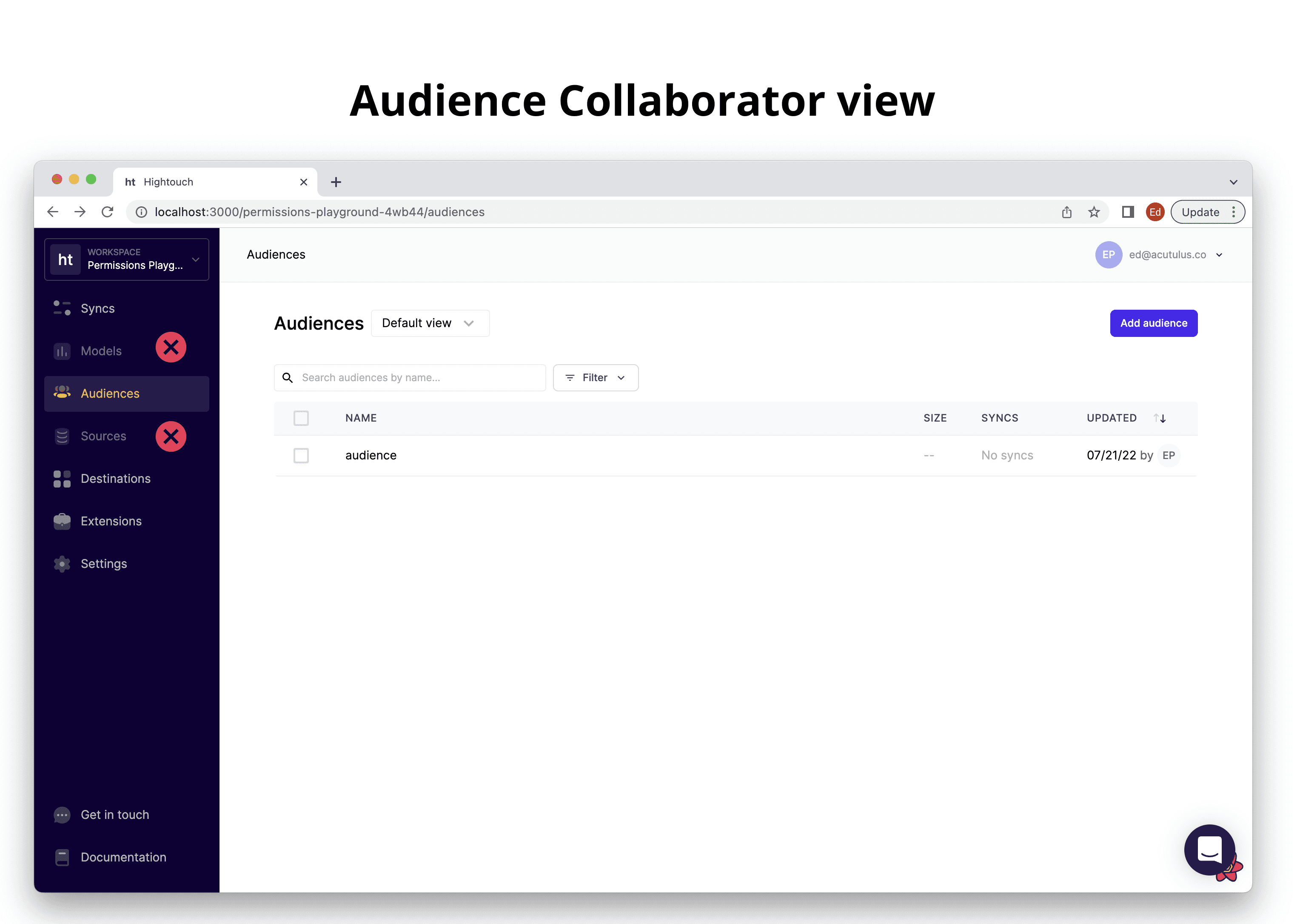
Audience Collaborator View
Our Governance Roadmap
With this launch, we're proud to stay on the leading edge of data governance for Reverse ETL platforms. We have an aggressive roadmap and plan to bring additional cutting-edge access management features to Hightouch, including tracking user activity, managing column-level controls, and more.
Next steps
These advanced access management features are available today for Business Tier customers. Jump to the Members tab in your application settings to get started. You'll be prompted to speak with a sales engineer to help you create your first custom policy. You can read more about these features in Docs.

















